- Wifi Hacker Software For Mac
- Wifi Password Hacker Software Mac
- Wifi Cracking Software Mac Pro
- Wifi Cracking Software Mac Download
- Wifi Cracking Software Mac High Sierra
- Wifi Password Cracking Software
If you want to know how to hack WiFi access point – just read this step by step aircrack-ng tutorial, run the verified commands and hack WiFi password easily.
MAC filtering, or MAC white- or blacklisting, is often used as a security measure to prevent non-whitelisted or blacklisted MAC addresses from connecting to the wireless network. MAC Address stands for media access control address and is a unique identifier assigned to your network interface. Explore the best Network software for Mac. Browse our catalog of over 50 000 mac apps. MacUpdate is serving app downloads since 1997.
With the help a these commands you will be able to hack WiFi AP (access points) that use WPA/WPA2-PSK (pre-shared key) encryption.
The basis of this method of hacking WiFi lies in capturing of the WPA/WPA2 authentication handshake and then cracking the PSK using aircrack-ng.

Wifi Hacker Software For Mac
How to hack WiFi – the action plan:
- Download and install the latest
aircrack-ng - Start the wireless interface in monitor mode using the
airmon-ng - Start the
airodump-ngon AP channel with filter for BSSID to collect authentication handshake - [Optional] Use the
aireplay-ngto deauthenticate the wireless client - Run the
aircrack-ngto hack the WiFi password by cracking the authentication handshake
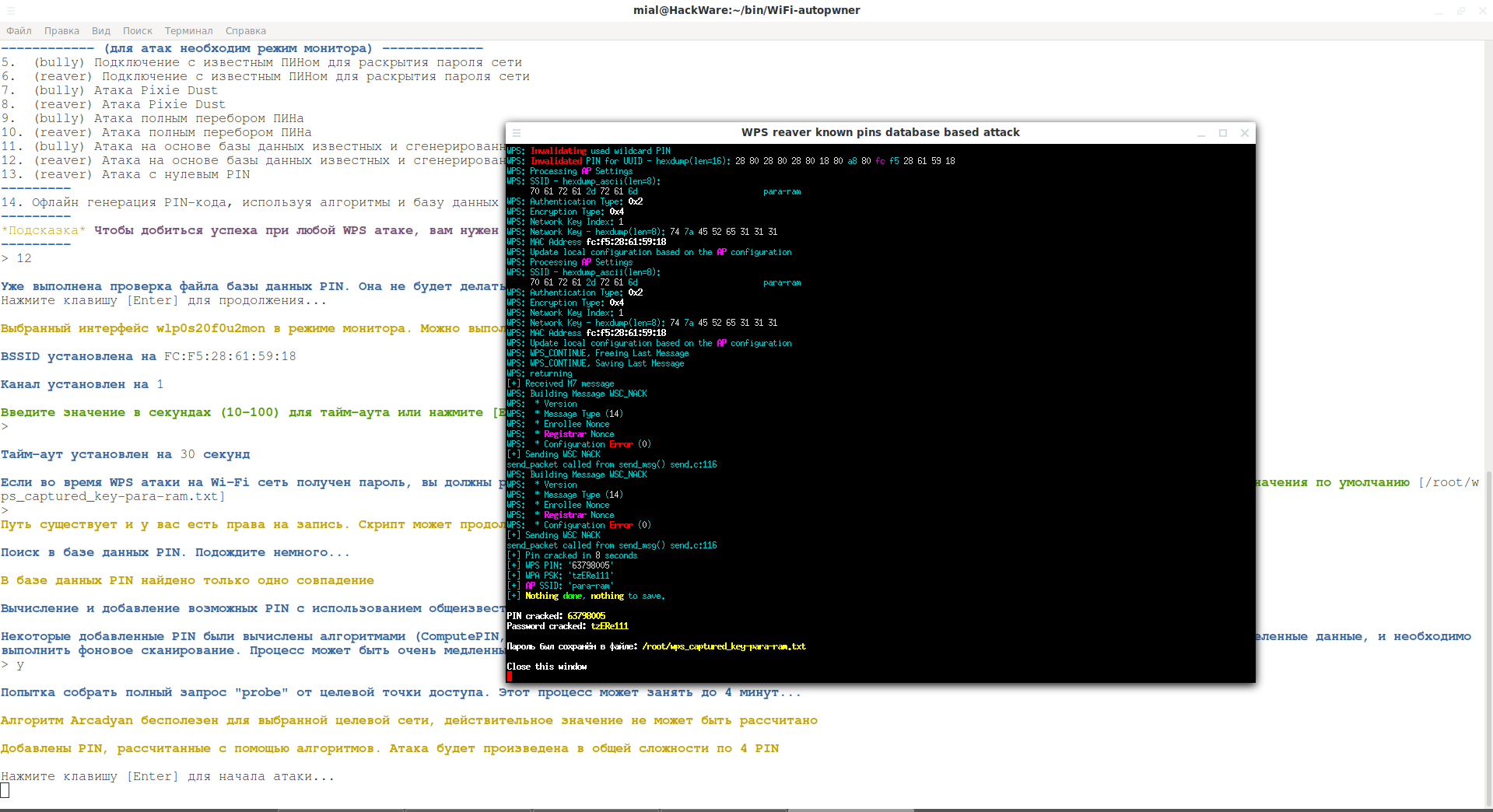
1. Aircrack-ng: Download and Install
The Latest Version Only: If you really want to hack WiFi – do not install the old aircrack-ng from your OS repositories. Download and compile the latest version manually.
Install the required dependencies:
Download and install the latest aircrack-ng (current version):
Ensure that you have installed the latest version of aircrack-ng:
2. Airmon-ng: Monitor Mode
Now it is required to start the wireless interface in monitor mode.Monitor mode allows a computer with a wireless network interface to monitor all traffic received from the wireless network.
What is especially important for us – monitor mode allows packets to be captured without having to associate with an access point.
Find and stop all the processes that use the wireless interface and may cause troubles:
Start the wireless interface in monitor mode:
In the example above the airmon-ng has created a new wireless interface called mon0 and enabled on it monitor mode.
So the correct interface name to use in the next parts of this tutorial is the mon0.
3. Airodump-ng: Authentication Handshake
Cool Tip: Want to have some 'fun'? Create a Linux fork bomb! One small string that is able to hang the whole system! Read more →
Now, when our wireless adapter is in monitor mode, we have a capability to see all the wireless traffic that passes by in the air.
This can be done with the airodump-ng command:
All of the visible APs are listed in the upper part of the screen and the clients are listed in the lower part of the screen:
Start the airodump-ng on AP channel with the filter for BSSID to collect the authentication handshake for the access point we are interested in:
| Option | Description |
|---|---|
-c | The channel for the wireless network |
--bssid | The MAC address of the access point |
-w | The file name prefix for the file which will contain authentication handshake |
mon0 | The wireless interface |
--ignore-negative-one | Fixes the ‘fixed channel : -1' error message |
airodump-ng captures a handshake.If you want to speed up this process – go to the step #4 and try to force wireless client reauthentication.
After some time you should see the WPA handshake: 00:11:22:33:44:55 in the top right-hand corner of the screen.
This means that the airodump-ng has successfully captured the handshake:
4. Aireplay-ng: Deauthenticate Client
Cool Tip: Want to stay anonymous? Learn how to use PROXY on the Linux command line. Read more →
If you can't wait till airodump-ng captures a handshake, you can send a message to the wireless client saying that it is no longer associated with the AP.
The wireless client will then hopefully reauthenticate with the AP and we'll capture the authentication handshake.
Send deauth to broadcast:

Send directed deauth (attack is more effective when it is targeted):
| Option | Description |
|---|---|
--deauth 100 | The number of de-authenticate frames you want to send (0 for unlimited) |
-a | The MAC address of the access point |
-c | The MAC address of the client |
mon0 | The wireless interface |
--ignore-negative-one | Fixes the ‘fixed channel : -1' error message |
Cool Tip: Need to hack WiFi password? Don't wast your time! Use 'John the Ripper' – the fastest password cracker! Read more →
5. Aircrack-ng: Hack WiFi Password
Unfortunately there is no way except brute force to break WPA/WPA2-PSK encryption.To hack WiFi password, you need a password dictionary.
And remember that this type of attack is only as good as your password dictionary.
You can download some dictionaries from here.
Crack the WPA/WPA2-PSK with the following command:
| Option | Description |
|---|---|
-w | The name of the dictionary file |
-b | The MAC address of the access point |
WPAcrack.cap | The name of the file that contains the authentication handshake |
Cool Tip: Password cracking often takes time. Combine aircrack-ng with 'John The Ripper' to pause/resume cracking whenever you want without loosing the progress! Read more → Door won't open from inside.
These days the Wi-Fi networks are more secure than the older days, These days most wireless access points use WPA(Wi-Fi Protection Access) 2 Pre Shared Key in order to secure the network. This WPA 2 uses a stronger encryption algorithm which is known as AES which is very difficult to crack.
When it comes to security nothing is 100% flawless and so as with WPA PSK 2. WPA PSK 2 has a vulnerability which is that the password in the encrypted form is shared by means of a 4-way handshake. When a user authenticates through the Access Point the user and the Access Point have to go through a 4-way Handshake in order to complete the authentication process. In Wi-Fi hacking, we capture the 4-way handshake packet and look for the encrypted key in those packets. After getting the encrypted key we try a specific wordlist in order to crack the encrypted password. Though there are many other ways as well to crack a wifi password the one with wordlist is the easiest to use and is widely used by the attackers.
Hacking Wi-Fi
1. List all the available network Interfaces.
The airmon-ng tool is used to work with network interfaces. Enter the following command to get the list of all the available network interfaces.
2. Monitor the desired network interface
The next step is to monitor the wireless network interface, so that we may see all the traffic that passes through the interface. airmon-ng command is used for the purpose.
Replace wlan0 with your desired wifi network and 1 with the desired channel number.
3. Capture the network interface traffic
Now as we are monitoring our wireless network interface, it's time to capture the traffic. To do so we will use airodump-ng tool. Enter the following command to display the captured information.
Note: Copy the bssid of the desired network.
Replace wlan0mon with the wireless interface which you want to use.
4. Capture required data from the specific network
Now, we have to attack a specific network, so in order to do that, we will capture the traffic on that network and will start the capturing of the 4-way handshake. Enter the following command to do that.
Here, 09:98:98:98:98:98 is the bssid of the network copied from the above step, -c 1 is the channel number, psk is the file in which the captured traffic would be written and wlan0mon is the network interface that is being monitored.
Wifi Password Hacker Software Mac
Note: Do not quit the command being executed in the terminal till the 6th step. Download the game ice cream.
5. De authenticate the client
Now, we have to de authenticate the client against the AP in case they're already authenticated. To do so we use aireplay-ng command. Enter the following command to de authenticate the client in the new terminal window.
Here, 09:98:98:98:98:98 is the bssid of the network, 100 is the number of de authenticate frames to be sent and wlan0mon is the network interface that is being monitored.
6. Verify the captured handshake file. Drivers toshiba satellite c655 s5512 specifications.
Now, our handshake file is captured successfully which can be confirmed with the 'ls' command.
Wifi Cracking Software Mac Pro
Now our handshake file is successfully captured.
Wifi Cracking Software Mac Download
7. Stop Wi-Fi interface monitoring
Now, we have successfully captured our handshake file and it's time to get our Wi-Fi interface back to its defaults. Enter the following command to stop monitoring the Wi-Fi interface.
8. Cracking password from the captured handshake file.
Now everything is done it's time to brute force the password. In order to get the password by means of a brute force attack, we need a wordlist and our handshake file. Inn order to generate a good wordlist use crunch utility in Kali Linux or use the one from predefined wordlists. and after that enter the following command in terminal.
Here,
- psk*.cap : It is the file which has the captured handshake file.
- wordlist: It is the wordlist that contains the password to be tested.
It will display key Found along with the key after successfully cracking the password.
Wifi Cracking Software Mac High Sierra
Recommended Posts:
Wifi Hacker Software For Mac
How to hack WiFi – the action plan:
- Download and install the latest
aircrack-ng - Start the wireless interface in monitor mode using the
airmon-ng - Start the
airodump-ngon AP channel with filter for BSSID to collect authentication handshake - [Optional] Use the
aireplay-ngto deauthenticate the wireless client - Run the
aircrack-ngto hack the WiFi password by cracking the authentication handshake
1. Aircrack-ng: Download and Install
The Latest Version Only: If you really want to hack WiFi – do not install the old aircrack-ng from your OS repositories. Download and compile the latest version manually.
Install the required dependencies:
Download and install the latest aircrack-ng (current version):
Ensure that you have installed the latest version of aircrack-ng:
2. Airmon-ng: Monitor Mode
Now it is required to start the wireless interface in monitor mode.Monitor mode allows a computer with a wireless network interface to monitor all traffic received from the wireless network.
What is especially important for us – monitor mode allows packets to be captured without having to associate with an access point.
Find and stop all the processes that use the wireless interface and may cause troubles:
Start the wireless interface in monitor mode:
In the example above the airmon-ng has created a new wireless interface called mon0 and enabled on it monitor mode.
So the correct interface name to use in the next parts of this tutorial is the mon0.
3. Airodump-ng: Authentication Handshake
Cool Tip: Want to have some 'fun'? Create a Linux fork bomb! One small string that is able to hang the whole system! Read more →
Now, when our wireless adapter is in monitor mode, we have a capability to see all the wireless traffic that passes by in the air.
This can be done with the airodump-ng command:
All of the visible APs are listed in the upper part of the screen and the clients are listed in the lower part of the screen:
Start the airodump-ng on AP channel with the filter for BSSID to collect the authentication handshake for the access point we are interested in:
| Option | Description |
|---|---|
-c | The channel for the wireless network |
--bssid | The MAC address of the access point |
-w | The file name prefix for the file which will contain authentication handshake |
mon0 | The wireless interface |
--ignore-negative-one | Fixes the ‘fixed channel : -1' error message |
airodump-ng captures a handshake.If you want to speed up this process – go to the step #4 and try to force wireless client reauthentication.
After some time you should see the WPA handshake: 00:11:22:33:44:55 in the top right-hand corner of the screen.
This means that the airodump-ng has successfully captured the handshake:
4. Aireplay-ng: Deauthenticate Client
Cool Tip: Want to stay anonymous? Learn how to use PROXY on the Linux command line. Read more →
If you can't wait till airodump-ng captures a handshake, you can send a message to the wireless client saying that it is no longer associated with the AP.
The wireless client will then hopefully reauthenticate with the AP and we'll capture the authentication handshake.
Send deauth to broadcast:
Send directed deauth (attack is more effective when it is targeted):
| Option | Description |
|---|---|
--deauth 100 | The number of de-authenticate frames you want to send (0 for unlimited) |
-a | The MAC address of the access point |
-c | The MAC address of the client |
mon0 | The wireless interface |
--ignore-negative-one | Fixes the ‘fixed channel : -1' error message |
Cool Tip: Need to hack WiFi password? Don't wast your time! Use 'John the Ripper' – the fastest password cracker! Read more →
5. Aircrack-ng: Hack WiFi Password
Unfortunately there is no way except brute force to break WPA/WPA2-PSK encryption.To hack WiFi password, you need a password dictionary.
And remember that this type of attack is only as good as your password dictionary.
You can download some dictionaries from here.
Crack the WPA/WPA2-PSK with the following command:
| Option | Description |
|---|---|
-w | The name of the dictionary file |
-b | The MAC address of the access point |
WPAcrack.cap | The name of the file that contains the authentication handshake |
Cool Tip: Password cracking often takes time. Combine aircrack-ng with 'John The Ripper' to pause/resume cracking whenever you want without loosing the progress! Read more → Door won't open from inside.
These days the Wi-Fi networks are more secure than the older days, These days most wireless access points use WPA(Wi-Fi Protection Access) 2 Pre Shared Key in order to secure the network. This WPA 2 uses a stronger encryption algorithm which is known as AES which is very difficult to crack.
When it comes to security nothing is 100% flawless and so as with WPA PSK 2. WPA PSK 2 has a vulnerability which is that the password in the encrypted form is shared by means of a 4-way handshake. When a user authenticates through the Access Point the user and the Access Point have to go through a 4-way Handshake in order to complete the authentication process. In Wi-Fi hacking, we capture the 4-way handshake packet and look for the encrypted key in those packets. After getting the encrypted key we try a specific wordlist in order to crack the encrypted password. Though there are many other ways as well to crack a wifi password the one with wordlist is the easiest to use and is widely used by the attackers.
Hacking Wi-Fi
1. List all the available network Interfaces.
The airmon-ng tool is used to work with network interfaces. Enter the following command to get the list of all the available network interfaces.
2. Monitor the desired network interface
The next step is to monitor the wireless network interface, so that we may see all the traffic that passes through the interface. airmon-ng command is used for the purpose.
Replace wlan0 with your desired wifi network and 1 with the desired channel number.
3. Capture the network interface traffic
Now as we are monitoring our wireless network interface, it's time to capture the traffic. To do so we will use airodump-ng tool. Enter the following command to display the captured information.
Note: Copy the bssid of the desired network.
Replace wlan0mon with the wireless interface which you want to use.
4. Capture required data from the specific network
Now, we have to attack a specific network, so in order to do that, we will capture the traffic on that network and will start the capturing of the 4-way handshake. Enter the following command to do that.
Here, 09:98:98:98:98:98 is the bssid of the network copied from the above step, -c 1 is the channel number, psk is the file in which the captured traffic would be written and wlan0mon is the network interface that is being monitored.
Wifi Password Hacker Software Mac
Note: Do not quit the command being executed in the terminal till the 6th step. Download the game ice cream.
5. De authenticate the client
Now, we have to de authenticate the client against the AP in case they're already authenticated. To do so we use aireplay-ng command. Enter the following command to de authenticate the client in the new terminal window.
Here, 09:98:98:98:98:98 is the bssid of the network, 100 is the number of de authenticate frames to be sent and wlan0mon is the network interface that is being monitored.
6. Verify the captured handshake file. Drivers toshiba satellite c655 s5512 specifications.
Now, our handshake file is captured successfully which can be confirmed with the 'ls' command.
Wifi Cracking Software Mac Pro
Now our handshake file is successfully captured.
Wifi Cracking Software Mac Download
7. Stop Wi-Fi interface monitoring
Now, we have successfully captured our handshake file and it's time to get our Wi-Fi interface back to its defaults. Enter the following command to stop monitoring the Wi-Fi interface.
8. Cracking password from the captured handshake file.
Now everything is done it's time to brute force the password. In order to get the password by means of a brute force attack, we need a wordlist and our handshake file. Inn order to generate a good wordlist use crunch utility in Kali Linux or use the one from predefined wordlists. and after that enter the following command in terminal.
Here,
- psk*.cap : It is the file which has the captured handshake file.
- wordlist: It is the wordlist that contains the password to be tested.
It will display key Found along with the key after successfully cracking the password.
Wifi Cracking Software Mac High Sierra
Recommended Posts:
Wifi Password Cracking Software
If you like GeeksforGeeks and would like to contribute, you can also write an article using contribute.geeksforgeeks.org or mail your article to contribute@geeksforgeeks.org. See your article appearing on the GeeksforGeeks main page and help other Geeks.
Please Improve this article if you find anything incorrect by clicking on the 'Improve Article' button below.
